
Enlarge (credit: Getty Images)
Ransomware has emerged as one of the top threats facing large organizations over the past few years, with researchers reporting a more than a fourfold increase in detections last year. A recent infection by a fairly new strain called LockBit explains why: after it ransacked one company’s poorly secured network in a matter of hours, leaders had no viable choice other than to pay the ransom.
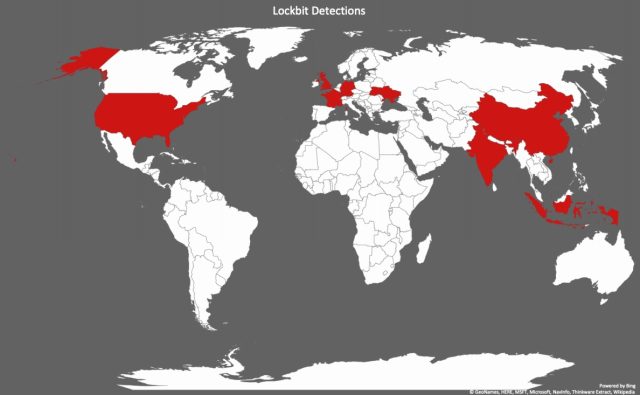
A report published by McAfee documents the effectiveness of this newcomer ransomware. Incident responders with Northwave Intelligent Security Operations aided in the analysis. LockBit is most prevalent in countries including the US, the UK, France, Germany, Ukraine, China, India, and Indonesia.
Attackers started out by researching potential targets with valuable data and the means to make big payouts when faced with the dim prospect of losing access to it. The attackers then used a list of words in hopes of gaining access to one of the accounts. Eventually, they hit the jackpot: an administrative account that had free rein over the entire network. The weak account password, combined with the lack of multi-factor authentication protection, gave the attackers all the system rights they needed.
Read 14 remaining paragraphs | Comments
from Biz & IT – Ars Technica https://ift.tt/3f7NhqY








0 comments:
Post a Comment