
Attackers from a group dubbed Poison Carp used one-click exploits and convincing social engineering to target iOS and Android phones belonging to Tibetan groups in a six-month campaign, researchers said. The attacks used mobile platforms to achieve a major escalation of the decade-long espionage hacks threatening the embattled religious community, researchers said.
The report was published on Tuesday by Citizen Lab, a group at the University of Toronto's Munk School that researches hacks on activists, ethnic groups, and others. The report said the attackers posed as New York Times journalists, Amnesty International researchers, and others to engage in conversations over the WhatsApp messenger with individuals from the Private Office of His Holiness the Dalai Lama, the Central Tibetan Administration, the Tibetan Parliament, and Tibetan human rights groups. In the course of the conversation, the attackers would include links to websites that hosted "one-click" exploits—meaning they required only a single click to infect vulnerable phones.
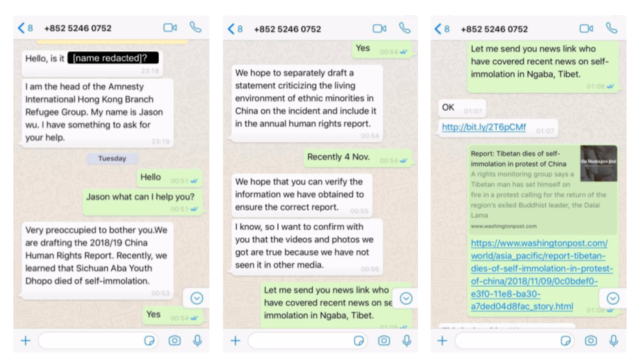
A social engineering attempt on November 13, 2018, shows the level of effort put into crafting a plausible deception. (credit: Citizen Lab)
Focused and persistent
None of the attacks Citizen Lab observed was successful, because the vulnerabilities exploited had already been patched on the iOS and Android devices that were attacked. Still, the attackers succeeded in getting eight of the 15 people they targeted to open malicious links, and bit.ly-shortened attack pages targeting iPhone users were clicked on 140 times. The research and coordination that went into bringing so many targeted people to the brink of exploitation suggest that the attackers behind the campaign—which ran from November 2018 to last May—were skilled and well organized.
Read 20 remaining paragraphs | Comments
from Biz & IT – Ars Technica https://ift.tt/2n2bV5x







0 comments:
Post a Comment